At The University of Baltimore, we provide knowledge that works. Get real-world career preparation and the hands-on experience employers demand at a fraction of the cost of other universities. Pick courses that fit your schedule and create an education tailored to your vision and needs. Welcome to UBalt!
It it safe to read e-mail on your phone? Check out how to avoid common snares.
Smartphone Security
Effective smartphone security requires physical and technical considerations. Follow the tips listed here to improve your phone's security.
Your phone may be setup to automatically access your personal accounts. Turning on lock security prevents others from being able to access your accounts, emails, texts, and photos. For better protection, enable the setting to automatically lock your phone after a period of inactivity.
For best protection, do not save your password in any app. The inconvenience of entering a password each time you access your email or bank account is nothing compared to the inconvenience if that information is compromised.
If your phone is stolen, lock security safeguards your information from being accessed.
Apps and system updates are regularly released. Some updates will address vulnerabilities. It's important that you install updates when prompted.
Shoulder surfing is a common social engineering technique used to obtain your PIN or password by looking over your shoulder. Once a shoulder surfer
has your password, they can steal your phone and access your accounts and information.
When entering your password, be aware of who can see your screen.
Jailbreaking or rooting may give your device more functionality, but it can also render your device more susceptible to malware. The risk is not worth the reward.
One of the most effective ways to protect sensitive data is to encrypt it. Most of the new mobile devices support a built-in hardware encryption that will make any data on your phone unreadable, unless your phone is unlocked. When a mobile device is lost or stolen, the data on that device cannot be read without the decryption key.
Today's devices are equipped with wireless communication technologies such as NFC, Bluetooth and Wireless chips, enabling your device to communicate with other devices. Disable the ones you don't use or disable them when you're not using them. Hackers can take advantage of open communications.
Uninstall any apps you no longer use.
The best encryption and best password protection won't stop it from being stolen. Never leave your phone unattend and don't lend it to strangers. If someone asks to make a call, make it for them. If you're dining outside in a busy spot, be careful about putting your phone on the table.
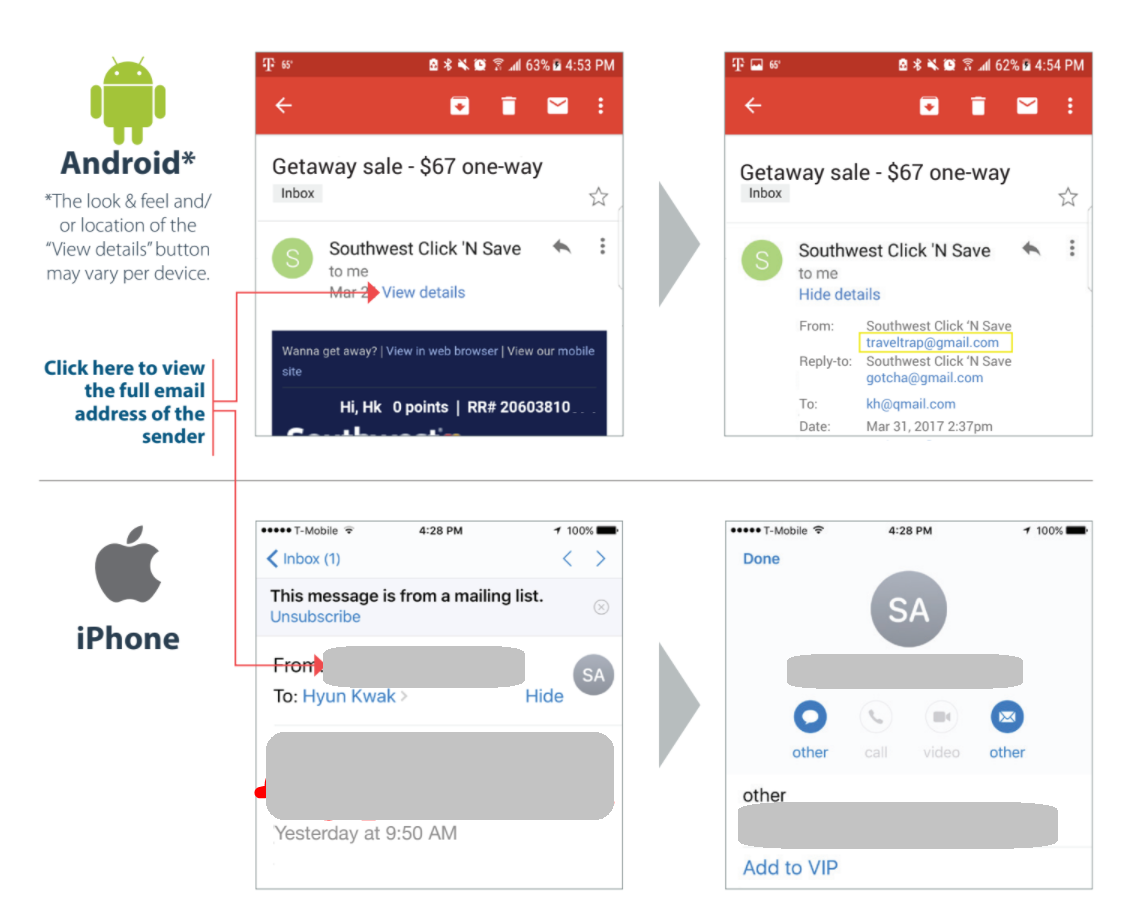
Opening Email On Your Phone?
Even on your phone, you need to avoid being phished. Follow these tips to ensure emails are legitimate before you respond to any calls for information or passwords.Phishing emails often try to create a sense of urgency and play off your emotions with warnings, deadlines or prizes. Counter that by responding deliberately.
- Check the sender's full email address (see below) before clicking on any links. Spoofed sender addresses can look similar to legitimate addresses but tend to contain typos or extra characters. Example, apple.au.co or aapple.com.
- Are you the only recipient? A real invoice or support request would not be addressed to a group.
- A reputable company is unlikely to first notify you of an account issue with a request to reset your password.
- Is your name on it? Phishing emails often do not specify the recipient’s name.
- Rather than responding to the email, go online, lookup company's website, then contact them using the information listed on their website. Do not follow the links in the email.